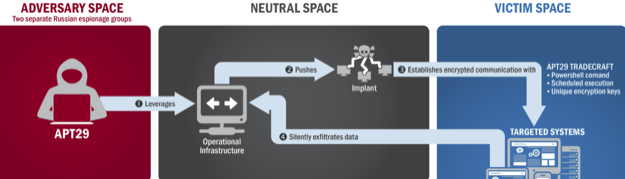
Crackers working for the Russian government broke into the computer system of “a U.S. political party” during the last election cycle. That’s the unsurprising top line conclusion of a joint report issued by the federal homeland security department and the FBI. Two separate teams working for Russian intelligence agencies phished more than a thousand party functionaries and eventually gained access to administrator level privileges on the target system.
Beneath that top line, though, lurks a fascinating, and ironic, description of how state-sanctioned crackers can penetrate workaday IT networks maintained by corporations and government agencies, and what can be done to stop them.
It’s worth reading, although number one of the top seven list of good security practices in the report seems like a no brainer: keep your software up to date…
Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
The irony lies in the fact that the FBI and other law enforcement and national security agencies not only routinely exploit such software vulnerabilities instead of quickly and publicly squashing such bugs, but also want technology companies to build back doors and weaken encryption to make that job easier.
You can’t have it both ways, as a recent congressional report pointed out (albeit with much handwringing over the need to try). Either the FBI and its fellow travellers are working 24/7 to plug security holes for everyone, or they’re playing on the same team as the Russian, Chinese and other state sponsored cyber spies who are routinely, and correctly, accused of subverting democratic processes and stomping out personal liberty at every opportunity.